Lab 2: Password Cracking
- First read this page then start working through the lab with the GitHub classroom link below.
- Github Classroom Link: https://classroom.github.com/a/HJdTmSRC
- Put your answers in the README.md file in the GitHub repository.
Objective
Learn about how passwords are cracked with the latest tools.
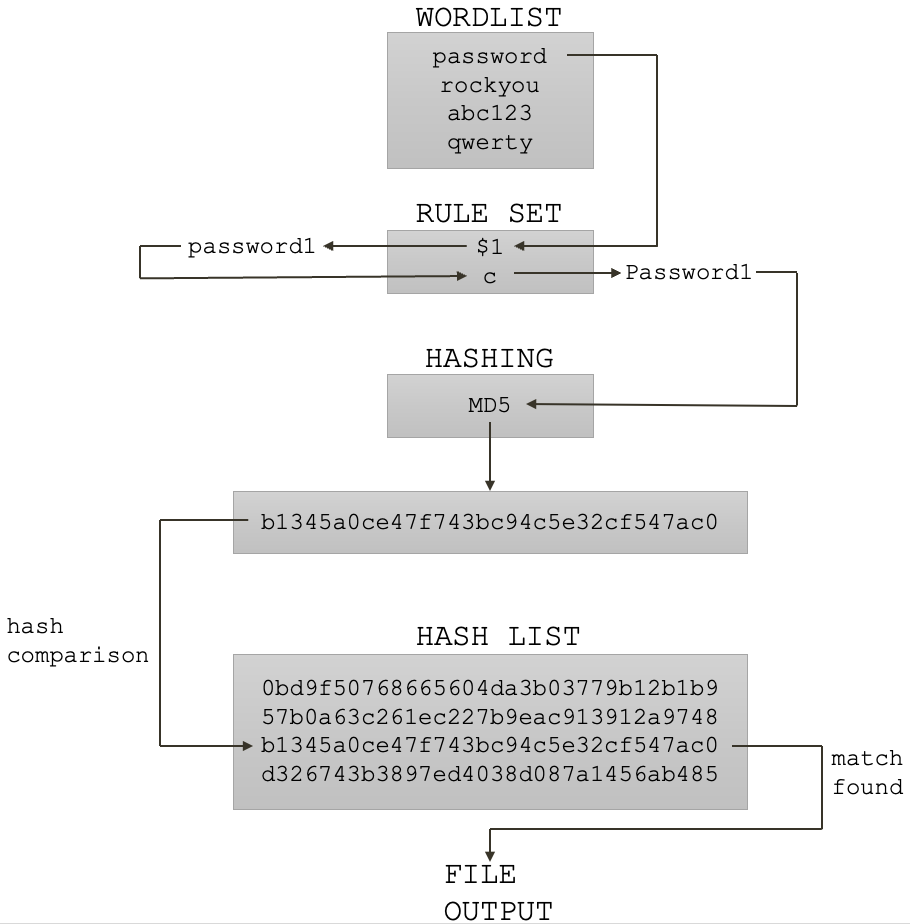
The password cracking process
- Create or use an existing list of potential passwords.
- Apply the same hashing algorithm that the system used to create the hash value.
- Compare that hash value to the one recovered from the system.
- If they match, you have cracked the password!
- If they do not match, try the next password.
Cracking Tool: hashcat

Mask attack (Brute-force)
Mask attack: Try all combinations from a given keyspace just like in Brute-Force attack, but more specific.
A mask is a simple string that configures the keyspace of the password candidate engine using placeholders.
Built-in charsets
- ?l = abcdefghijklmnopqrstuvwxyz
- ?u = ABCDEFGHIJKLMNOPQRSTUVWXYZ
- ?d = 0123456789
- ?h = 0123456789abcdef
- ?H = 0123456789ABCDEF
- ?s = !"#$%&'()*+,-./:;<=>?@[\]^_`{}~
- ?a = ?l?u?d?s
- ?b = 0x00 - 0xff
Example masks
- 7 lower case letters ?l?l?l?l?l?l?l
- 6 lower case followed by two digits ?l?l?l?l?l?l?d?d
- 6 lower case followed by special characters ?l?l?l?l?l?l?s?s
Try this
- Copy the example0.hash file to your home directory.
$ cp /usr/share/doc/hashcat-data/examples/example0.hash ~ - View the hashes listed in the
example0.hashfile. And count the number of hashes in the file.$ cat example0.hash $ wc -l example0.hash - Run the
hashcatprogram to attempt to crack some of the passwords in theexample0.hashfile. We will use the-m 0to specify theMD5hash algorithm. We will use the-a 3flag for attack mode 3, which is the "Mask Attack". We will provide the hash file to crack, and the mask which instructshashcatwhich character sets to use in which position in the passwords that it guesses. We will start with trying a seven lower case letter password. Hashcat will print out cracked passwords like this:e691253bdabbf723a9644e0ed1a6d31b:shuzman, the hash value followed by a semicolon and then the password.$ hashcat -m 0 -a 3 example0.hash ?l?l?l?l?l?l?l - If it pauses you can select
sto print the status and thenfto finish. - When it is complete you can view the passwords that you cracked by looking at your hashcat potfile.
$ cat ~/.local/share/hashcat/hashcat.potfile - How many passwords did you crack? Hint
wc -l ~/.local/share/hashcat/hashcat.potfile - Next lets try to add another lower case letter to our mask so it now generates passwords with 8 lower case letters:
?l?l?l?l?l?l?l?l. Re-run step 3 with this new mask. - You can stop this run after a few minutes by typing
qto quit. - How many did you crack this time? Hint: re-run the word count command in step 6, but subtract the results from the first run.
- Now change your mask to generate passwords with 6 lower case letters followed by 2 digits at the end. How many did you crack?
- How many brute-force passwords are attempted with the ?l?l?l?l?l?l?l mask?
- How about the ?l?l?l?l?l?l?d?d mask?
Dictionary attack (aka. Wordlist attack)
Dictionary Attack: All that is needed is to read line by line from a textfile (aka "dictionary" or "wordlist") and try each line as a password candidate.
- Copy the example.dict file to your home directory.
$ cp /usr/share/doc/hashcat-data/examples/example.dict ~ - View the some of the words in the
example.dictfile. And count the number of words in the file.$ tail -1000 example.dict $ wc -l example.dict - Run the
hashcatprogram to attempt to crack some of the passwords in theexample0.hashfile. We will use the-m 0to specify theMD5hash algorithm. We will use the-a 0flag for attack mode 0, which is the "Dictionary Attack". We will provide the hash file to crack, and the dictionary from which to gather attempted password guesses.$ hashcat -m 0 -a 0 example0.hash example.dict - If it pauses you can select
sto print the status and thenfto finish. - When it is complete you can view the passwords that you cracked by looking at your hashcat potfile.
$ cat ~/.local/share/hashcat/hashcat.potfile - How many passwords did you crack? Hint
wc -l ~/.local/share/hashcat/hashcat.potfileand compare with previous count.
Rule based attack
Rule Based Attack: The rule-based attack (-a 0 with one or more -r rules files) is one of the most complicated of all the attack modes. The reason for this is very simple. The rule-based attack is like a programming language designed for password candidate generation. It has functions to modify, cut or extend words and has conditional operators to skip some, etc. That makes it the most flexible, accurate and efficient attack.
- Copy the dive.rule file to your home directory.
$ cp /usr/share/hashcat/rules/dive.rule ~ - View the some of the rules in the
dive.rulefile. And count the number of rules in the file.$ head -100 dive.rule $ wc -l dive.rule - Run the
hashcatprogram to attempt to crack some of the passwords in theexample0.hashfile. We will use the-m 0to specify theMD5hash algorithm. We will use the-a 0flag for attack mode 0, which is the "Dictionary Attack" but we also specify a-r dive.rulewhich turns on rules. We will provide the hash file to crack, and the dictionary from which to gather attempted password guesses.$ hashcat -m 0 -a 0 -r dive.rule example0.hash example.dict - You can type q to quit after it runs for a few minutes.
- When it is complete you can view the passwords that you cracked by looking at your hashcat potfile.
$ cat ~/.local/share/hashcat/hashcat.potfile - How many passwords did you crack? Hint
wc -l ~/.local/share/hashcat/hashcat.potfileand compare with previous count. - Why did the rules based attack crack more passwords than the dictionary attack, even though it uses the same dictionary?
- Now lets try this with a different word list. The infamous
rockyou.txt.$ cp /usr/share/wordlists/rockyou.txt.gz ~ $ gzip -d rockyou.txt.gz - Take a look at the rockyou word list.
$ head -100 rockyou.txt - Notice that the list is not in alphabetical order like the example.dict. It is in order by most common passwords. Do you think this will improve the performance of you password cracking attempts?
- Give it a try:
$ hashcat -m 0 -a 0 -r dive.rule example0.hash rockyou.txt - You can type q to quit after it runs for a few minutes.
- When it is complete you can view the passwords that you cracked by looking at your hashcat potfile.
$ cat ~/.local/share/hashcat/hashcat.potfile - How many passwords did you crack? Hint
wc -l ~/.local/share/hashcat/hashcat.potfileand compare with previous count.
 Slack for Q&A
Slack for Q&A